
Information
How to remove HEROSET ransomware
What is Heroset?
Heroset is a program that belongs to the Djvu ransomware family. It was discovered by Michael Gillespie. The main purpose of Heroset is to encrypt files (make them unusable) and to force victims to pay a ransom/buy a decryption tool. It places the "_readme.txt" file (a ransom note) in every folder that contains encrypted files, it also renames all those files. Heroset adds the ".heroset" extension to every encrypted file, for example, it renames a file named "1.jpg" to "1.jpg.heroset" and so on.
As stated in the "_readme.txt" file, Heroset encrypts all files (including photos, databases, documents and so on) with a strong encryption that can be decrypted only with the right decryption key and tool. In order to purchase them, victims must to pay a ransom of $980. However, cyber criminals who developed Heroset offer a 50% discount for victims who will contact them in no more than 72 hours after encryption. To contact them, victims have to write an email to gorentos@bitmessage.ch or stoneland@firemail.cc address. Another way to contact Heroset's developers is via Telegram by writing to @datarestore. One way or another, it is required send them the appointed personal ID too. In order to avoid having to contact and/or pay them, we recommend to try using an offline decryption tool. However, it may help only if there was no Internet connection (or remote server that cyber criminals use was not responding) during the encryption process. There is no other way to decrypt files encrypted by Heroset for free. Ransomware-type programs cause strong encryptions that can be decrypted only with the right tools that cyber criminals have. If there was a data backup created before encryption, then we recommend to restore all files from there.
Screenshot of a message encouraging users to pay a ransom to decrypt their compromised data:
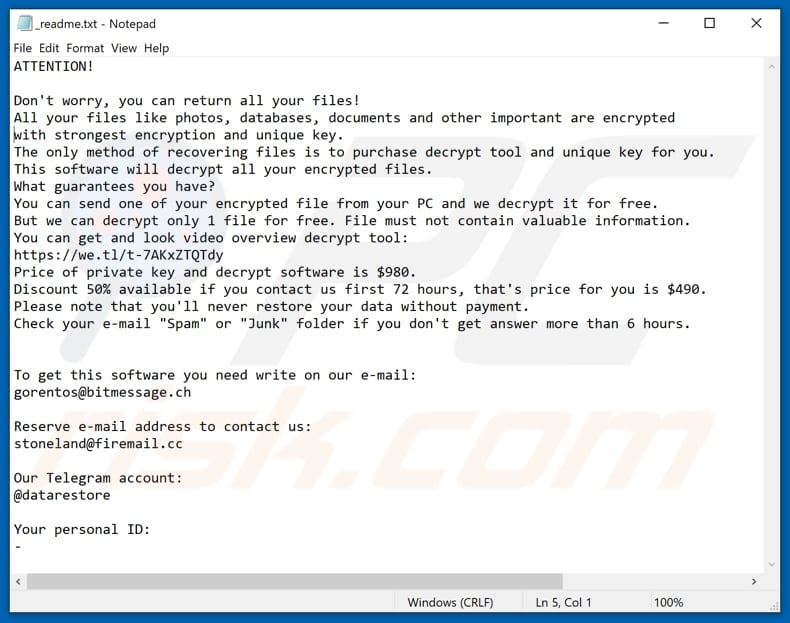
The number of ransowmare-type programs is growing by the days, Poret, Buran and Luboversova148 are just a couple of other programs of this type. Typically, these are designed to encrypt data and force victims to pay a ransom. The main and most common differences between these malicious programs are the price of a decryption (ransom size) and cryptography algorithm (symmetric or asymmetric) that is used to lock files. Another common thing is that most of these programs are impossible to 'crack', in other words, successful decryptions can be performed only with the right tools. That is why it is important to have a data backup and to keep it stored on some remote server or unplugged storage device.
How did ransomware infect my computer?
There are some popular ways to spread ransomware-type programs/to trick people into installing them. Typically, cyber criminals proliferate malware through spam campaigns, trojans, unofficial software updating or software 'cracking' tools and untrustworthy software download sources. They use email spam campaigns by sending emails that contain attachments. For example, they send some Microsoft Office document or PDF documents, archive files like ZIP, RAR, executables (.exe and other executable files), JavaScript files and so on. The main goal of these emails/spam campaigns is to trick people into opening the attachment which causes download and installation of some high-risk malware. Trojans are malicious programs that usually are designed to spread other programs of this kind. In other words, if a computer is infected with a trojan, then it is very likely that it will download and install more malware. Fake software updaters usually infect systems by downloading and installing computer infections instead of updates, fixes, or by exploiting outdated software's bugs, flaws. Various activation tools that supposed to allow their users to activate licensed for free often are designed to infect computers with malware. Peer-to-peer (P2P) networks, free file hosting pages, freeware download websites, third party downloaders and other similar tools can be and are used as tools to proliferate malicious programs too. Cyber criminals upload malicious files that are disguised as normal, harmless and hope that someone will download and open them. If opened, these files infect computers.
MOST VIEWED ARTICLES
LATEST ARTICLES
13 Feb, 2021
13 Feb, 2021