
Information
Racoon Malware Steals Your Data From Nearly 60 App
An infostealing malware that is relatively new on cybercriminal forums can extract sensitive data from about 60 applications on a targeted computer.
The malware scene is constantly changing and what used to be top of the line a few years ago is now available for a modest price by comparison and a much richer set of features.
Raccoon infostealer was observed in the wild for the first time almost a year ago and has gained quickly gained in popularity due to its low price and generous features
Unsophisticated yet good enough
Also known as Legion, Mohazo, and Racealer, the malware was initially promoted only on Russian-speaking forums but it soon made its entrance in the English-speaking space. The malware was first seen in the wild April 2019 and it is distributed under the MaaS (malware-as-a-service) model for $75/week or $200/month.
For this money, the attackers get access to an administration panel that lets them customize the malware, access stolen data, and download the builds of the malware.
This model is widely adopted today because it opens the door to a larger number of cybercriminal customers, many lacking the proper technical knowledge but compensating in business experience.
An analysis from CyberArk found that it is written in C++ and is far from being a complex tool. However, it can steal sensitive and confidential information from almost 60 programs (browsers, cryptocurrency wallets, email and FTP clients).
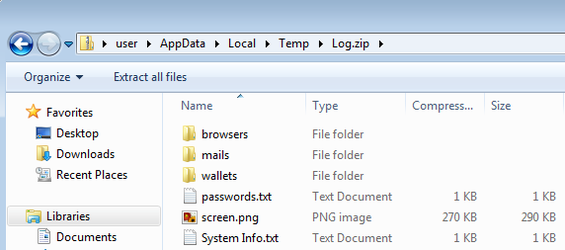
All the popular browsers (Google Chrome, Mozilla Firefox, Microsoft Edge, Internet Explorer, Opera, Vivaldi, Waterfox, SeaMonkey, UC Browser) are on the list of targets along with more than 20 other solutions, which are robbed of cookies, history, and autofill information.
Hot cryptocurrency apps like Electrum, Ethereum, Exodus, Jaxx, and Monero, are of interest, searching for their wallet files in the default locations. However, Raccoon also can scan the system to grab wallet.dat files regardless of where they are stored.
From the email client software category, Raccoon looks for data from at least Thunderbird, Outlook, and Foxmail.
In a report today CyberArk researchers say that this infostealer relies on the same procedure to steal the data: locate and copy the file with the sensitive info, apply extraction and decryption routines, and placing the info in a text file ready for exfiltration.
Additional capabilities in the malware include collecting system details (OS version and architecture, language, hardware info, enumerate installed apps).
Attackers can also customize Raccoon's configuration file to snap pictures of the infected systems' screens. Additionally, the malware can act as a dropper for other malicious files, essentially turning it into a stage-one attack tool.
This type of malware is not necessarily used for immediate benefits as it is useful for increasing permissions on the system or for moving to other computers on the network.
"After fulfilling all his stealing capabilities, it gathers all the files that it wrote to temp folder into one zip file named Log.zip. Now all it has to do is send the zip file back to the C&C server and delete its trace" - CyberArk
Like all malware riding the popularity wave, Raccoon is actively improved with fixes for various issues, new functions, and capabilities.
While analyzing one sample, researchers noticed new versions being released, which extended support for targeted apps, adding FileZilla and UC Browser, and adding the option to encrypt malware builds straight from the administration panel and getting them in DLL form.
Raccoon does not use any special techniques to extract information from targeted programs, yet it is one of the most popular infostealers on cybercriminal forums. Recorded Future notes in a report from July 2019 that it was one of the best selling malware in the underground economy.
Three months later, researchers at Cybereason also note that the malware was enjoying positive reviews from the community, many actors praising and endorsing the malware. Established members, though, criticized its simplicity and lacking in features present in tools of the same feather.
However, despite its simplicity, its infection count is at hundreds of thousands of computers across the world.
This shows that technical features are not necessarily what attackers are after when choosing a malicious tool but a good balance between price, accessibility, and capabilities.
"What used to be reserved for more sophisticated attackers, now even novice players can buy stealers like Raccoon with the intention of getting their hands on an organization’s sensitive data" CyberArk
Among the delivery methods used for Raccoon, security researchers observed it being dropped via exploit kits, phishing, and PUA (potentially unwanted applications).
CyberArk's report today comes with indicators of compromise (IoC) and a YARA rule to catch a Raccoon infection.
MOST VIEWED ARTICLES
LATEST ARTICLES
13 Feb, 2021
13 Feb, 2021


